The presidential campaign team of Donald Trump has acknowledged that their systems have been compromised and that some of their internal communications were unlawfully accessed by foreign agents.
Trump’s team has connected this to Iran in response to a Microsoft report that described how a “high-ranking official on the presidential campaign trail” had been targeted.
Politico, a news site, revealed that it had obtained a set of data from an AOL email account that was only identified by Robert and was anonymous. Research on Ohio Senator JD Vance, who is currently Trump’s running mate, and his prior negative statements on the 45th President of the United States were among the details revealed.
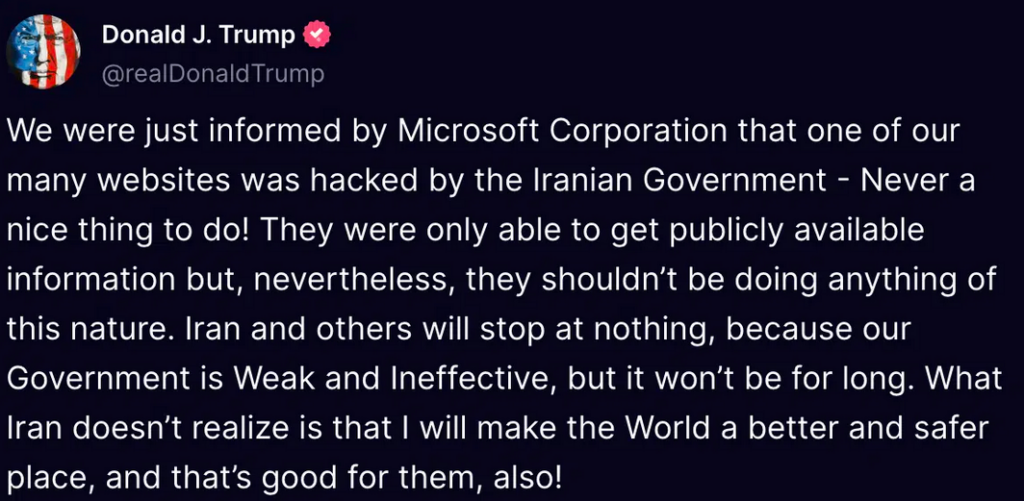
Trump played down the significance of the hacking event on his Truth Social platform, acknowledging it only as “publicly available information” that the attackers had obtained.
According to reports, the attack was carried out by Iran’s Islamic Revolutionary Guard Corps, which used a hacked account belonging to a former top adviser to send a spearphishing email to a “high-ranking official.” It is alleged that the email included a link that would cause traffic to pass via a domain controlled by the hackers and then be redirected to the intended, authentic website.
Since 2016, the number of foreign actors has grown.
Iranian agents are committed to swaying the U.S. presidential election in November, according to the Microsoft Threat Analysis Center report’s findings. The threat actors use a variety of strategies, such as creating fake news websites and purporting to provide localized updates and insights. Although disinformation may have unintended implications in swing states, the efforts are directed towards both political extremes.
According to Microsoft’s analysis, since the 2016 election—the scene of the previous high-profile cyberattack—the number of covert operations from foreign sources has increased.
On that occasion, the Democratic National Committee’s internal cables were leaked, and it is thought that Russian hackers were behind it.